Mobile Banking Risk Identification and Mitigation
by Jerome F. Combs, Supervisory Examiner, Federal Reserve Bank of Minneapolis
Mobile devices — smartphones and tablets — are easy to use and can be taken almost anywhere. They provide users with easy access to personal and financial data via applications that allow the movement and storage of data locally on the devices and/or allow data to be sent to and stored with a third party. But they can also be lost or stolen, infected with malware, and used as a vehicle for fraud. Even so, smartphones and tablets are here to stay. The way consumers use them may change over time, but it is clear that mobile banking via smartphones and tablets is on trend to grow rapidly in the coming years.
Mobile device software provider Malauzai Software, Inc., released data on August 14, 2013, that confirmed the growing use of mobile banking applications. The report indicated that "For banks and credit unions who have been live a minimum of 12 months, the average month-over-month growth rate is 4.19 percent. The best in class number is 11.56 percent, with several banks and credit unions topping 10 percent. Organic growth is strong and can be attributed to the general growth of mobile smart phone handsets as well as these financial institutions making mobile part of all of their marketing campaigns."1 In another report based on a 2012 survey of 1,115 U.S. consumers, the Aite Group forecasted that the number of mobile banking users would continue to grow significantly, as shown in Figure 1.2
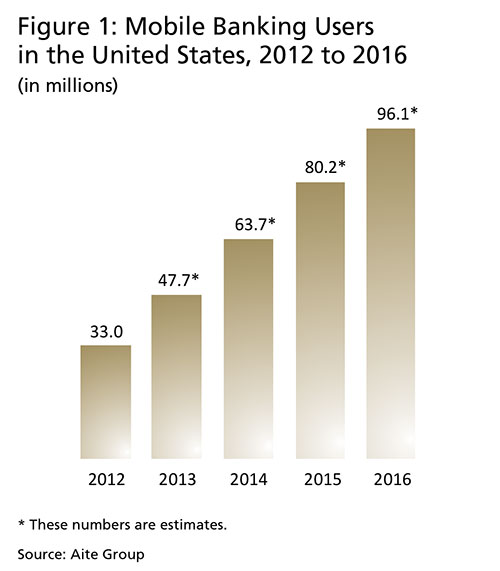
Many community banks recognize the value of mobile banking — it provides them with avenues and opportunities to reach geographically remote or rural markets, to focus on new markets, to innovate, to overcome infrastructure limitations and improve efficiency, to access payment systems, or even simply to retain market share. However, the rapid growth of mobile banking introduces security risk and privacy issues that must be managed. It is critical that banks anticipate and recognize risk in order to protect customers and their own reputation. This article reviews mobile banking risks and risk mitigation solutions, discusses regulatory guidance, and suggests ways to implement mobile banking risk assessment and ongoing risk management strategies at community banks.
What Is Mobile Banking?
To understand the risks associated with mobile banking, it is necessary to separate mobile banking from the broader arena of mobile financial services and products. Mobile financial services involves the use of a mobile device for transfers (originating wire or automated clearing house (ACH) transactions), marketing, banking, or payments (person-to-person or person-to-business transactions), while mobile banking allows customers of an insured depository institution to conduct banking activities, such as checking balances, receiving account alerts, or making bill payments, through a smartphone or tablet. Mobile financial services, of which mobile banking is a subset, involve nonbank third parties. As such, this article focuses only on mobile banking because of the unique and ongoing risks faced by financial institutions that offer this service.
Mobile Banking Risk Identification
Providing consumers with the ability to transact banking business using a mobile device — with security settings of the customer's choosing — places an increasing amount of control over sensitive financial data into consumers' hands. The net loss of control over this information makes it more difficult for the bank to assess risks and implement effective risk mitigation strategies.
To understand mobile banking risk, it is important to understand the three most common delivery channels (many institutions offer all three channels to reach the greatest number of customers):
- Text messaging/short message service (SMS)
- Mobile-enabled Internet browser
- Mobile applications
Text Messaging/SMS
SMS, commonly referred to as "texting," is limited in the number of characters used. It is most often used as an alert and inquiry delivery channel. SMS is used to make mobile banking available to users of older cell phones that do not have web browsers or applications. SMS messages are sent in cleartext over widely used telecommunications networks, with no encryption capabilities. Also, the customer's account identifier is stored in an SMS message, which means that there is the possibility of misuse if the phone is lost or stolen. SMS mobile banking users can also be susceptible to receiving misleading or socially engineered messages that could prompt them to reveal account information. Because of the limited utility of older cell phones and the growth of smartphones, the use of SMS for mobile banking is fading.
Mobile-Enabled Internet Browser
Mobile Internet banking via a mobile-enabled Internet browser is an extension of the online banking channel. Customers can navigate to a website on a smartphone or tablet via the embedded browser in much the same way that they can access a site from a personal computer. Although banking from a mobile device using a mobile-enabled Internet browser is open to the same vulnerabilities as banking from a personal computer, it is usually harder to see and use security features on a mobile device.
Mobile Applications
Mobile application banking uses a custom-designed software application installed on a smartphone or tablet that provides for a more user-friendly interface than is possible with either SMS or mobile browser-based banking. As such, this is the fastest growing delivery channel for mobile banking. However, this channel introduces risks that may arise if third parties write the code for these applications, as well as the possibility that the applications can be compromised if customers install rogue, corrupted, or malicious software.
The storage of customer data on a phone or tablet presents the opportunity for misuse if the device is lost or stolen. In addition, likely attacks against mobile banking include fraudulent requests (e.g., phishing e-mails or SMS messages) that appear to require the installation of a new application or security feature from a bank, or malware that can steal credentials by prompting users to type an account number and password.
A good source of information related to mobile security risks is the Open Web Application Security Project (OWASP), a worldwide nonprofit organization focused on improving the security of web application software. It has developed a list of what it views as the top 10 risks arising from the use of mobile applications. Highlights of some of the risks that may be most relevant for community banks are summarized below:3
- Insecure data storage. Threats include lost or stolen phones or tablets and the possibility of malware gaining access to the device.
- Weak server side controls. This pertains to the back-end computers that the mobile banking process needs to use. The security, authentication, and general controls related to these computers need to be strong.
- Insufficient transport layer protection. This refers to the lack of data encryption when data travel over public networks.
- Poor authorization and authentication. Some mobile applications rely only on unchanging, potentially compromised values for authentication, and some identification data can remain even after data wipes or resets.
Mobile banking introduces new security risks, threats, and challenges to financial institutions. Although no mitigation scheme can completely eliminate risk, banks should develop practices to effectively safeguard the mobile banking process. By staying abreast of security risks and developing effective mobile banking practices, a bank can reduce and better manage its legal, operational, and reputational risks.
Mobile Banking Risk Mitigation
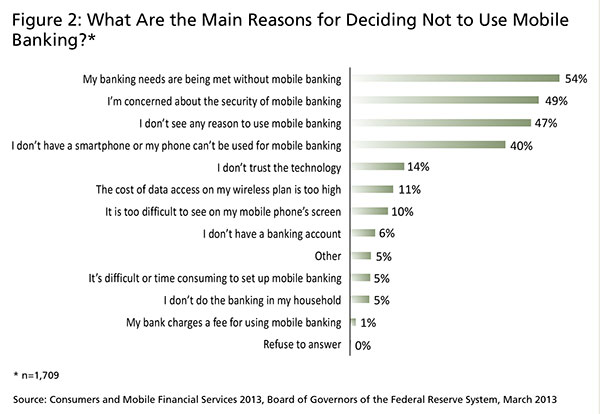
With the convenience and rapid promotion of mobile banking, it may seem puzzling that many customers are still reluctant to embrace it. In a March 2013 Federal Reserve System survey,4 consumers were asked "What are the main reasons you decided not to use mobile banking?" The most commonly cited reason was security, such as data loss, fraud, identity theft, and other risks (Figure 2).
A careful reading of the OWASP list of risks faced by banks offering mobile banking reveals that many of these risks are aligned with the risks that are perceived by their customers, as noted in Figure 2. Accordingly, the actions a bank takes to mitigate its risk could positively influence customers' sense of security and their willingness to adopt this service.
As part of its Mobile Security Project, OWASP has also outlined suggested risk mitigation solutions — a list of its top 10 mobile controls — that address the mobile risks outlined above.5 The controls are discussed below from the perspective of the bank providing mobile financial services. For example, highlights of some controls a bank should consider when having an application developed for mobile banking include the following:
- Identify and protect sensitive data on the mobile device. Store sensitive financial and consumer data on another computer instead of on the mobile device. If data are stored on the device, use strong encryption technology provided by a trusted source.
- Ensure that sensitive data are protected while in transit. Assume nothing is secure. Mobile banking applications should enforce the use of an end-to-end secure channel such as secure sockets layer/transport layer security (SSL/TLS) and use strong encryption.
- Implement user authentication, authorization, and session management correctly. Require appropriate-strength user authentication, for example, multifactor versus strong authentication. Physical tokens or voice, fingerprint, or behavioral authentication factors may be appropriate.
- Secure data integration with third-party services and applications. Ensure that mobile banking applications and code are tested, come from a reliable source, have supported maintenance, and have no back-end malware (for example, Trojans).
Mobile Banking Risk Assessment
Once bank management understands the risks posed by mobile banking and the potential strategies for mitigating those risks at a high level, the final step in the process is to apply those general concepts to the specific products and services offered by the bank. This begins with completing a risk assessment based on bank-specific factors. To complete an effective risk assessment, bank management should:
- Understand the network architecture and mobile banking technology solution(s) being used.
- Know how the mobile banking application is designed, understand what features are being used, and be aware of the threats to the application.
- Identify the wireless transmission protocols and data transmission media being used.
- Understand what data the application stores and processes, as well as how this information is stored.
- Know the methods of attack to which the application is vulnerable and which are the most common. Identify controls to prevent attacks and/or data loss.
- Have a robust vendor management process. If a third party (or parties) is involved in offering mobile banking, complete a thorough due diligence to understand all the preceding risk assessment elements as they apply to that third party.
One possibility is to use a data-centric approach to risk assessment and ongoing risk management. Data discovery and classification are two essential initiatives that lay the foundation for protecting data no matter where this information resides. If a financial institution does not know what kind of data it has or where they reside, it cannot apply the appropriate policies and controls to protect this information.6 This especially applies to mobile banking and the risks and controls discussed in this article. The following table is a simple data classification chart that a bank can fill out that could be used to identify critical data and associated control requirements based on the implementation of a mobile banking solution.
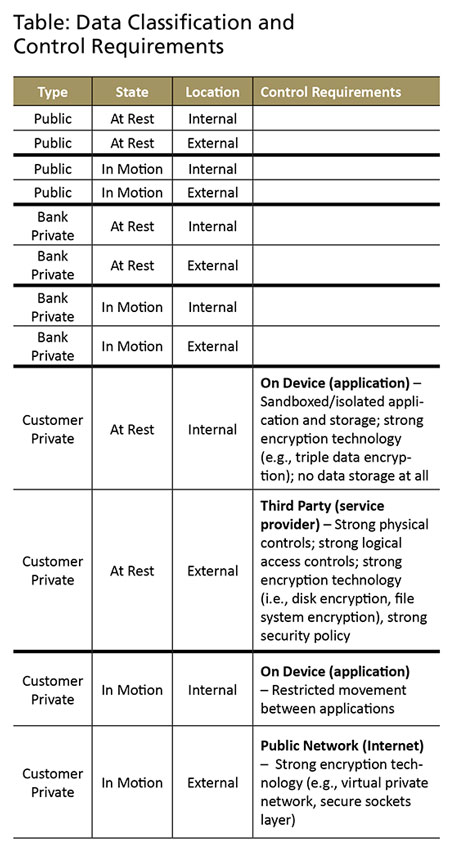
For example, consider a financial institution that implements mobile banking and uses a mobile banking application provided by a third-party vendor. A customer will use a mobile device, but the actual device and operating system will not be known by the financial institution. What is known is that the customer's private data will be in motion on a public network between the device and the vendor (that is, this information will be located externally). The customer's private data will rest in storage at the vendor (also located externally).
Mobile Banking Risk Controls
Based on information provided in this article, what control requirements should a bank consider? The answer depends on the type of mobile banking technology being implemented. See the table on the previous page for sample requirements. These are samples only; specific mobile banking implementations and risk assessments may indicate less or more controls.
Options to consider include a secure end-to-end delivery channel on the public network, strong authentication on the device, and strong secure mobile application coding and testing standards for the mobile banking application. If a financial institution cannot meet its controls requirements (including assessment of the controls used by a vendor) at any point, a reassessment is necessary. A financial institution should be able to complete an assessment and provide ongoing risk management by answering four critical questions:
- Where is it (for example, data type, hardware, software, and process)? An effective risk assessment process should help answer this question.
- Who owns it (for example, data type, hardware, software, process, and policy)? It is critical to assign ownership in order to establish responsibility and accountability.
- How do you know? Is there a significant security gap? Are controls working effectively? Are they the right controls? Effective risk assessment and audit processes help answer these questions.
- What does "normal" look like? Ensure that monitoring and reporting processes related to data flow and transactions are in place in order to effectively identify abnormal behavior that could indicate malicious activity.
Following this type of process will help ensure that control gaps are identified, action plans to mitigate gaps are developed, and residual risk is acceptable. This process also provides for effective audit validation and feedback related to the intended control environment, leading to a safer and more successful implementation.
Conclusion
Whether it is because of demand from customers or a desire to enter new markets, many community banks are beginning to offer mobile financial services to their customers. As with all new products, bankers need to understand the mobile banking environment being used and the associated risks. Effective risk identification and implementation of mitigation controls and processes based on the data type, state, and location are key to achieving this objective. With the proper strategy and risk management elements in place, both the bank and its customers should experience a safer mobile banking environment. 7
Regulatory Guidance for Mobile Banking
In addition to sources of information from industry groups and associations, regulatory guidance that is pertinent to mobile banking is also available. While not as technical in nature as the OWASP guidance, it nevertheless provides support and direction related to the same control areas. Related guidance includes:
Federal Reserve Supervision and Regulation (SR) Letters:a
- SR letter 13-19/CA letter 13-21, "Guidance on Managing Outsourcing Risk"
- SR letter 11-9, "Interagency Supplement to Authentication in an Internet Banking Environment"
- SR letter 05-19, "Interagency Guidance on Authentication in an Internet Banking Environment"
- SR letter 01-15, "Standards for Safeguarding Customer Information"
- SR letter 98-9, "Assessment of Information Technology in Risk-Focused Frameworks for the Supervision of Community Banks and Large Complex Banking Organizations"
Federal Financial Institutions Examination Council (FFIEC) Information Technology Booklets:b
- Information Security
- Outsourcing Technology Services
- Business Continuity Planning
- E-Banking
- Audit
- a SR letters are available at www.federalreserve.gov/bankinforeg/srletters/srletters.htm.

- b FFIEC IT booklets are available at ithandbook.ffiec.gov/it-booklets.aspx.

Back to top
-
1
Malauzai Software, Inc., "Monkey Insights: Mobile Banking Smart Device Usage," August 2013, available at malauzai.com/docs/monkeyinsights_0813.pdf.

-
2
Ron Shevlin, "Mobile Banking Forecast: Smartphone and Table Use in the United States" report summary, Aite Group, December 17, 2012, available at
www.aitegroup.com/report/mobile-banking-forecast-smartphone-and-tablet-use-united-states.

-
3
The full list of the top 10 mobile application risks is available at www.owasp.org/index.php/Projects/OWASP_Mobile_Security_Project_-_Top_Ten_Mobile_Risks.

- 4 See www.federalreserve.gov/econresdata/mobile-devices/files/consumers-and-mobile-financial-services-report-201303.pdf.
-
5
The full list of the top 10 mobile controls is available at www.owasp.org/index.php/OWASP_Mobile_Security_Project#tab=Top_Ten_Mobile_Controls (May 22,
2013).

-
6
SC Magazine
Vendor Webcast, "Rethink Data Classification: Identify Your Data, Know Your Data," September 19, 2013, available at
www.scmagazine.com/rethink-data-classification-identify-your-data-know-your-data/article/311972/.

- 7 For a broader discussion about adding new services, see Teresa Curran, "Considerations When Introducing a New Product or Service at a Community Bank," Community Banking Connections, First Quarter 2013, available at www.cbcfrs.org/articles/2013/Q1/Considerations-When-Introducing-A-New-Product.cfm.
