November 2024
Security in the Cloud: A Discussion with the Regulators
by Ray Bolton, Risk Management Specialist, Supervision and Regulation, Federal Reserve Bank of Chicago
Cloud technology is an ever-evolving, on-demand delivery system used in the modern business environment that has become commonplace in many industries. The financial services industry is no exception, having significantly increased its adoption of cloud technology in recent years. According to the 2023 State of Financial Services in Cloud report from the Cloud Security Alliance, "98% of respondents cited that their organization is using some form of cloud computing, up from 91% in 2020."1
With such a clear increase in cloud technology adoption, it should come as little surprise that threat actors are increasingly targeting cloud environments with their attacks. A 2024 report from CrowdStrike, a U.S. cybersecurity technology company, notes the following: "As predicted, cloud environment intrusions increased by 75% from 2022 to 2023, with cloud-conscious cases increasing by 110% and cloud-agnostic cases increasing by 60%" (Figure 1).2 Further intensifying the risk to banks, Mandiant, a U.S. cybersecurity firm and a subsidiary of Google, reported that the financial services industry is the most targeted industry for cyberattacks, with 17.3 percent of all investigated cases (Figure 2). 3
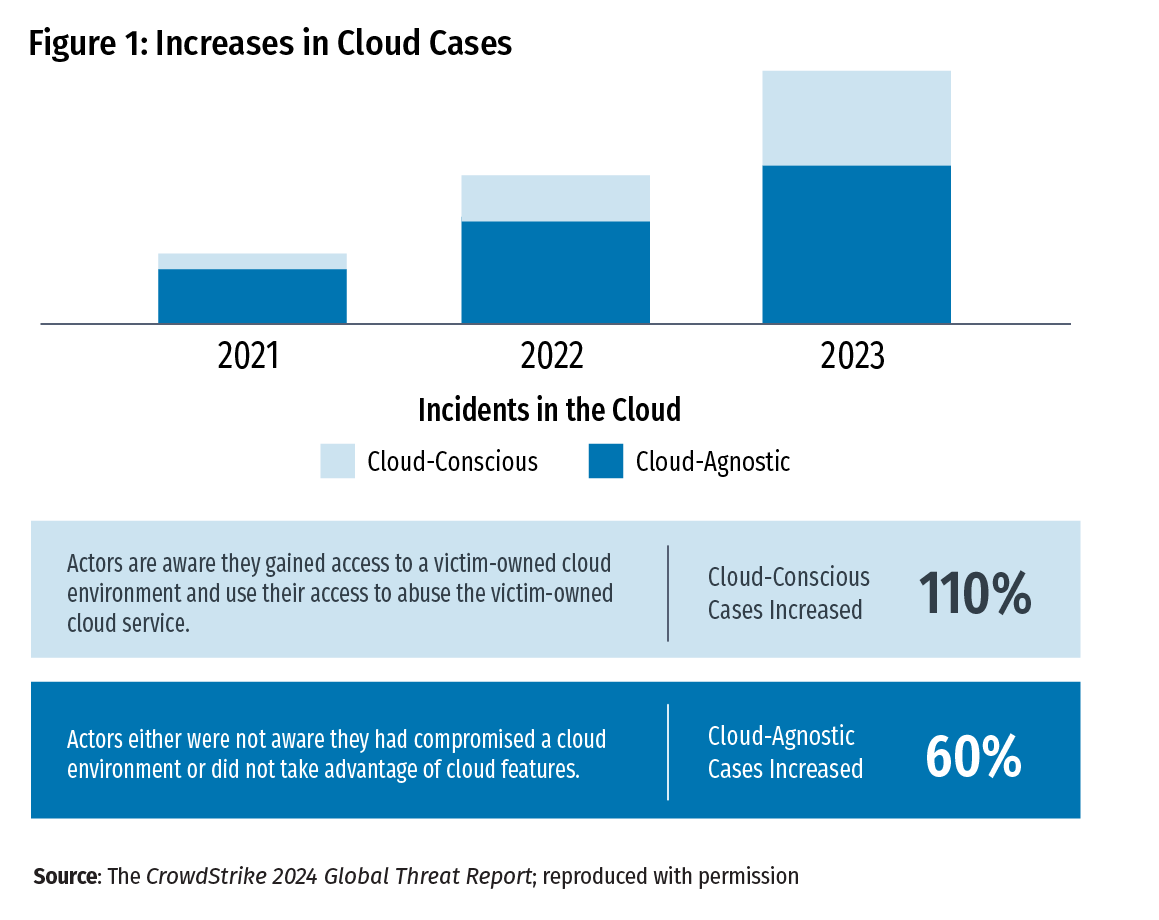
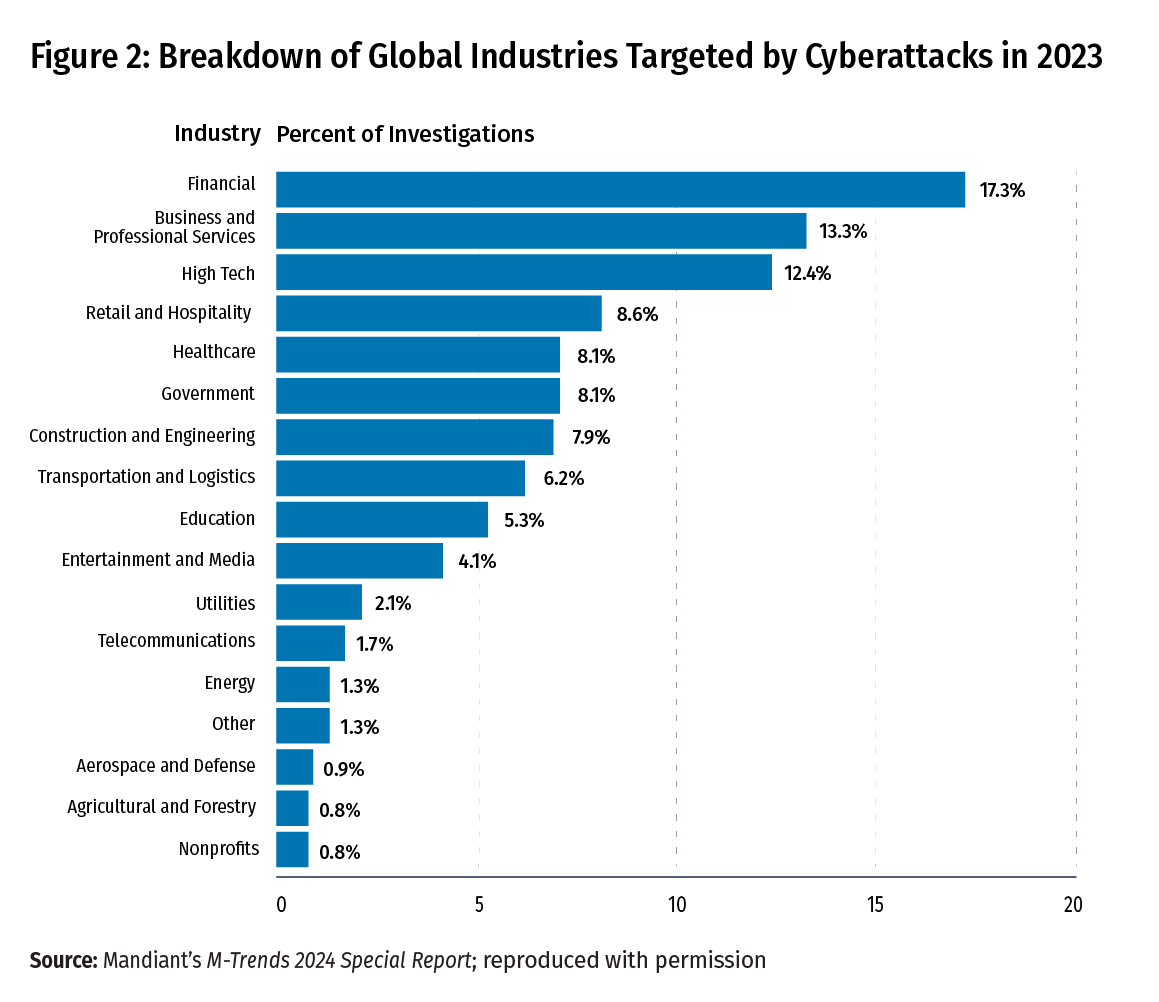
The combination of the increased adoption of cloud technology by the financial services industry and the prevalence of cyberattacks on cloud environments sets up a clear need for community banks to understand the risks of this type of operating environment and implement effective practices to ensure the confidentiality, integrity, and availability of their systems and data.
Industry Practices
The Federal Financial Institutions Examination Council (FFIEC) released the “Security in a Cloud Computing Environment” statement in 2020, detailing many effective risk management practices banks should implement to better defend against cyberattacks targeting cloud environments.4 The following list is a selection of the risk management practices that are critical to financial institutions.
- Governance: A bank’s board of directors and senior management should ensure any discussion about moving to a cloud environment aligns with the bank’s overall information technology (IT) strategy and risk appetite. While cloud computing services can offer many benefits, shifting to a cloud environment does not transfer the risk out of the bank. An appropriate level of governance should be determined before taking any action to transition to the cloud environment.
- Due Diligence and Ongoing Monitoring: Before engaging with a cloud service provider (CSP), management should conduct appropriate due diligence to identify any risks, including security considerations and controls unique to cloud computing environments. Management should ensure those risks are mitigated and, once engaged with a CSP, should continue to monitor the CSP for appropriate security.
- Contracts: Management should ensure contracts between the bank and the CSP clearly define the terms and responsibilities of both parties. Contracts are a critical step in ensuring that both parties have clear expectations and should detail which party is responsible for the configuration and management of system access rights, security monitoring, system updates, and other key security considerations. Operational resilience and incident response capabilities should also be considered.
- Identity and Access Management: A bank should implement strong controls for identity and access management, including limiting account privileges, implementing multifactor authentication (MFA), frequently updating and reviewing account access rights, monitoring activity, and requiring privileged users to have unique credentials for each segment of the network.
- Configuration: Cloud environments can entail security control configurations and processes that differ from those of traditional network architectures. Management should ensure that security tools within cloud resources are appropriately configured to avoid unauthorized access to nonpublic data. Additionally, regular testing of configurations, tools, and monitoring systems is a key consideration to ensure they are operating as expected.
- Inventory: Management should ensure that all assets within a cloud computing environment are appropriately inventoried and that a consistent, repeatable process is developed for identifying cloud assets. Appropriate and thorough decommissioning and destruction practices for cloud assets should also be developed and implemented, with clear data deletion time frames and methods established in the service contract.
While bankers should consider these practices, they should also review the practices contained within the “Security in a Cloud Computing Environment” statement to help defend against cyber incidents and reduce the impact of cyber incidents on their banks’ cloud assets.
Additionally, community banks should consult “Third-Party Risk Management: A Guide for Community Banks.”5 This guide was developed by the federal banking agencies6 and includes sound risk management principles for banking organizations to consider when developing and implementing risk management practices for third-party relationships, such as relationships with CSPs.
Experts' Perspectives

Several experts from the Federal Reserve System were interviewed for this article and provided additional perspectives on security practices for cloud environments — Scott Krause, cybersecurity supervision specialist at the Federal Reserve Bank of Richmond, Mark Townson, cybersecurity risk specialist at the Federal Reserve Bank of St. Louis, and Michelle Zhang, senior cybersecurity supervision specialist at the Federal Reserve Bank of Chicago. These experts provided their thoughts on a range of industry practices and insights on cloud cybersecurity from a regulatory perspective.
The FFIEC’s “Security in a Cloud Computing Environment” statement is directed at a broad range of institutions and provides an overview of strong practices for banks to take to secure their cloud environments. What would you say is most important from a community bank perspective?
Scott: Know what you have. For an organization of almost any size, the idea of cloud computing is no longer an abstract or potential consideration — it is how we do business. Whether it’s the formal use of a server in a cloud environment, back-office check imaging, or human resources and customer relationship management services being provided, community banking organizations (CBOs) face different types of risk. Just as you run discovery scans to identify what is on your network, it is also practical to review purchase orders to understand what services are being used externally.
Knowing what you have is a precursor to managing cloud assets effectively. While not every technology exposes the potential for funds transfers or theft, understanding the risk associated is possible once you have identified that asset. For example, ineffective implementation of MFA may expose a bank to social media risks if a former employee uses old credentials to post something on the bank’s behalf. Once you know what you have, you should ensure fundamental practices are in place to leverage built-in capabilities: Automated patching, backup and recovery, and even MFA are often available by default and can significantly strengthen your environment.
Mark: One of the most critical aspects for community banks considering moving or expanding into the cloud computing environment is third-party risk management.7 Community banks often rely heavily on third-party CSPs because of limited in-house IT resources. Ensuring robust third-party risk management practices can help mitigate potential vulnerabilities introduced by these external partners. CBOs should conduct thorough due diligence before selecting a CSP and critically assess a CSP’s security controls, compliance with relevant regulations, and ability to protect sensitive data.
Michelle: Taking the proactive approach to build a security-first culture is essential in today’s business environment. Cybersecurity, including cloud security, is a top priority that needs to be a company-wide focus. Security is everyone’s job, from the board of directors and senior management ensuring governance and controls over cloud security during and after migration to collaboration among cross-functional leaders and bank department heads. Security should be built into the bank’s culture, and it’s a good idea to implement routine cybersecurity awareness training such as periodic phishing exercises for all employees.
Threat actors are often looking for targets that will give them the biggest payday. Do community banks have as much to worry about as larger financial institutions?
Michelle: Absolutely. Financial institutions big and small are targeted, even though the reasoning behind the attacks may be different. Threat actors may target community banks based on the belief that their cybersecurity resources and skill sets may be limited and their internal controls will not be as robust as those of larger institutions.
Mark: With community banks expanding their technological footprint and their reliance on third-party vendors, they do face many of the same threats as larger financial institutions because of the perception of weaker security controls. Threat actors often perceive community banks as having less sophisticated security measures than larger institutions. This perception can make them attractive targets for attacks that exploit potential vulnerabilities. Ransomware attacks, specifically, do not discriminate based on the asset size of an institution. Cybercriminals target community banks for ransom payments, knowing that the disruption of services can push smaller banks to pay quickly to restore operations.
Scott: Why do bank robbers rob banks? “Because that’s where the money is.”8 Threat actors do not evaluate a potential target by completing a comprehensive risk analysis of the bank’s balance sheet and cybersecurity strength but rather by looking for known exploitable weaknesses and then seeing what opportunities those may provide. There are search engine tools that provide open-source intelligence on the 4.2 billion IP (Internet Protocol) addresses on the internet — where can those paths lead? While a hacker may not specifically target your organization, you may be collateral damage in an attack directed against a service provider or indirectly exposed because of dependencies in their environment (e.g., the DynDNS incident in 2016).9
Additionally, service providers may have hundreds or thousands of customers or entities, or more, connecting to their network. Even though your network may be secure, if the hosting environment is shared, another bank with lower standards may provide the initial entry point. Understanding the controls that protect multitenant environments and mitigate lateral movement is critical to ensuring that another organization’s lack of security doesn’t impact the security of your organization.
Because of their size, geographic limitations, and financial constraints, and for other reasons, community banks often have a limited number of IT staff members who are overseeing multiple aspects of the IT environment. How can management ensure proper consideration is given to security in the cloud while operating under these constraints?
Mark: Management at community banks can take several strategic steps to ensure proper consideration of security in the cloud while operating under resource constraints. An example would include choosing reputable CSPs that offer robust security features and compliance certifications (e.g., Service Organization Control (SOC) Type 210 and International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) 27001).11 Banks can also rely on the CSP's built-in security measures to off-load some, but not all, of the security responsibilities. Overall, I think a sound approach internally is to focus on the security basics. Community banks need to ensure that fundamental security practices are implemented first, such as strong password policies, MFA, and patch management. These basics can significantly reduce vulnerabilities and minimize the threat landscape of the organization.
Scott: Cybersecurity demands that staff members’ skills continue to evolve. At the outset, organizations should ensure that they have a plan outlining where internal staff resources are going to be used and the activities that are going to be outsourced. Once a workforce plan is identified, hire for the future, not the past. If you expect to be growing the business in cloud environments or through additional service providers, consider someone who has experience managing those relationships relative to the security and regulatory obligations of the bank. Finally, leave room in an agile workforce for employees to learn and explore emerging roles. Someone who spends 110 percent of their time fixing PC, server, and network issues will likely not be able to prepare for the bank’s future needs. Conversely, if only 90 percent of a staff member’s time is dedicated to day-to-day activities, that will allow 10 percent of their time to be used to prepare for the future and prevent new issues from arising.
Michelle: Community banks can use their size to their advantage by moving faster and being more agile than larger organizations. I agree with Mark that community banks should combat these cloud security threats by focusing on the essentials. CBOs can implement strong access control measures, monitor and analyze their environment, encrypt data both at rest and in transit, implement regular security evaluations and penetration testing, and implement routine comprehensive employee training. Finally, a bank should review, update, and test the incident response plan.
With a limited number of IT staff members overseeing multiple aspects of a bank’s IT environment, it is important for the bank’s various stakeholders to understand the need to focus on creating a strong security posture. Forming stronger, more intentional partnerships with cross-functional leaders can help build security into every aspect of a bank’s IT environment. Investing in tools such as intrusion detection systems and partnering with managed security service providers (MSSPs) can ensure a bank’s security remains effective and proactive.
It is often difficult for smaller institutions to hold much power in contract negotiations because of the immense size and influence of certain CSPs. How can community banks better ensure they have a meaningful say in contracts with providers?
Mark: A good first step that banks can take is to evaluate multiple CSPs to compare their contract terms, service offerings, and willingness to negotiate. This competitive assessment can provide leverage and identify providers that are more willing to meet the bank’s requirements. Another great practice is to refer to regulatory standards and supervisory guidelines during negotiations. CSPs familiar with the regulatory environment will understand the importance of incorporating these guidelines into the contract and will give the bank firm ground to stand on when discussing products and service offerings.
Michelle: It is always of the utmost importance to carefully review contracts, specifically around the shared responsibility model, to ensure that all grounds are covered and that a bank’s security and risk requirements as well as regulatory compliance are met. It is essential to vet these vendors carefully to ensure that they have strong cybersecurity practices in place. Community banks should also regularly review their vendor contracts to ensure that they include cybersecurity requirements and that vendors are held accountable for any security breaches. Major CSPs often have divisions and representatives specifically working with small and medium-sized businesses, which can be a starting point to address unique concerns. There are also MSSPs and software-as-a-service products targeted at smaller financial institutions.
Scott: Just as you wouldn’t settle for buying a car that doesn’t fit your needs, you shouldn’t be compelled to invest in a technology that doesn’t meet your bank’s security and legal requirements. If you know that you are going to have to drive in snow, then four-wheel drive, good tires, and antilock brakes are bare minimums. With your service provider, ensuring regulatory standards, compliance attestations, and the ability to perform ongoing due diligence can provide some similar protections. While the business from your bank may not be significant compared with that from a service provider’s overall customer base, there are ways to ensure that the technology fits your needs. This isn’t just around financial transactions either — inventorying your tools objectively will highlight where you may have exposure on your network or have opportunities to consolidate platforms.
Additionally, the availability of systems, applications, and data is a key security aspect of any engagement. Partnering business objectives for sustainability with those for third-party cyber risk management can lead to increased effectiveness of both contingency and incident response.
Are there any final points you want to share with the community banking audience?
Scott: More than anything, thank you for the things that you do for our communities. The services that you provide enrich the people that live and work in your District and strengthen our culture. Just as our communities are stronger together, cloud-based assets provide ties to resources beyond those community banks would normally have access to. Similar to loan requirements, understanding what cloud assets are in place and how they are being managed, along with ensuring basic standards, will help bolster community banks’ future potential.
Michelle: Vigilance and proactive measures are key to guarding data from fast-moving cloud security threats. Key areas of growing concern that cloud security teams should prioritize in the coming year are attacks on cloud-based artificial intelligence platforms, software supply chain risks, and cloud-native malware. By maintaining awareness of cloud assets and threats while staying agile to implement strategic defenses, community banks can considerably minimize risks and safeguard data in the cloud environment.
Mark: In cloud environments, security is a shared responsibility between a bank and a CSP. Community banks need to ensure there are clear lines of responsibility regarding which security controls are managed by their provider and which controls are the bank’s responsibility. A provider typically manages the security of the cloud infrastructure, while the bank is responsible for securing the data, user access, and applications. Community banks need to ensure detailed service-level agreements and contracts are in place to specify the security responsibilities of each party.
Conclusion
Cloud tools and services can offer many benefits to community banks, including as-needed scalability, cost savings, and access to cutting-edge technologies that might otherwise be unrealistic for a bank to obtain in-house. As with all aspects of the banking world, however, a bank’s adoption of the cloud environment comes with its share of risks. As more and more critical business and sensitive information is migrated to the cloud, cyberthreat actors shift their focus to this environment to search for the biggest payday. By implementing the strong security risk management practices discussed in this article, community bankers can leverage the benefits of cloud services while significantly reducing their risk.
- 1 The report is available at https://cloudsecurityalliance.org/artifacts/state-of-financial-services-in-cloud.
- 2 The CrowdStrike 2024 Global Threat Report is available at www.crowdstrike.com/global-threat-report/.
- 3 See Mandiant’s M-Trends 2024 Special Report, available at https://cloud.google.com/security/resources/m-trends?utm_source=ads-in-product&utm_medium=mandiant&utm_campaign=FY24-Q1-global-MAND942-website-dl-dgcsm-m-trends-2024&utm_content=-&utm_term=-&hl=en.
- 4 The FFIEC statement is available at www.ffiec.gov/press/PDF/FFIEC_Cloud_Computing_Statement.pdf.
- 5 For more information, see “Third-Party Risk Management A Guide for Community Banks,” May 2024, available at www.federalreserve.gov/publications/files/third-party-risk-management-guide-20240503.pdf.
- 6 The Board of Governors of the Federal Reserve System, the Federal Deposit Insurance Corporation, and the Office of the Comptroller of the Currency are collectively referred to as the federal banking agencies.
- 7 For more information on third-party risk management, see “Community Banking Connections Promo: Supplemental Interagency Guide for Community Banks on Third-Party Risk,” Community Banking Connections, Third Release 2024, available at www.cbcfrs.org/Articles/2024/R3/third-party-risk-guide.
- 8 This quote is attributed to famous American bank robber Willie Sutton.
- 9 The DynDNS incident referenced was a significant distributed denial of service attack that took place on October 21, 2016. More information is available at http://mse238blog.stanford.edu/2018/07/clairemw/the-2016-dyn-attack-and-its-lessons-for-iot-security/.
- 10 More information on SOC 2 reports is available at www.aicpa-cima.com/topic/audit-assurance/audit-and-assurance-greater-than-soc-2.
- 11 More information on ISO/IEC 27001 is available at www.iso.org/standard/27001#What%20Is%20ISO/IEC%2027001?.
